Mobile Application Security Essentials: A Comprehensive Guide for Flutter Apps
29 December 2023Today, we are witnessing a significant increase in the popularity of mobile applications, driven by the growth of smartphones and mobile devices. Communication, entertainment, management, access to information from all over the world, financial services, health, and other aspects of daily life can be more or less related to mobile tools, and people of all ages are increasingly open to taking such a chance.
But there is a dark side to the story: as the popularity of mobile apps grows, so does the number of threats, and keeping users safe is one of the most essential tasks companies face, especially as cybercriminals become more sophisticated in their methods of fraud.
Methods to protect against these types of threats must be customized to the kind of application because while many of the general principles of design and management remain the same, specific implementations and security strategies can vary by technology and platform.
In this short guide, we will focus on applications developed with Flutter, a framework from Google.
Key Security Threats – the most common examples
Understanding potential threats is the first step to protecting your applications. Unfortunately, there are numerous of them, and the creativity of criminals can be surprising – malware, phishing, man-in-the-middle (MitM), or authentication attacks are just a few examples. Fortunately, user education is also increasing, and more awareness means better data protection.
Among the most crucial security issues highlighted by respondents were:
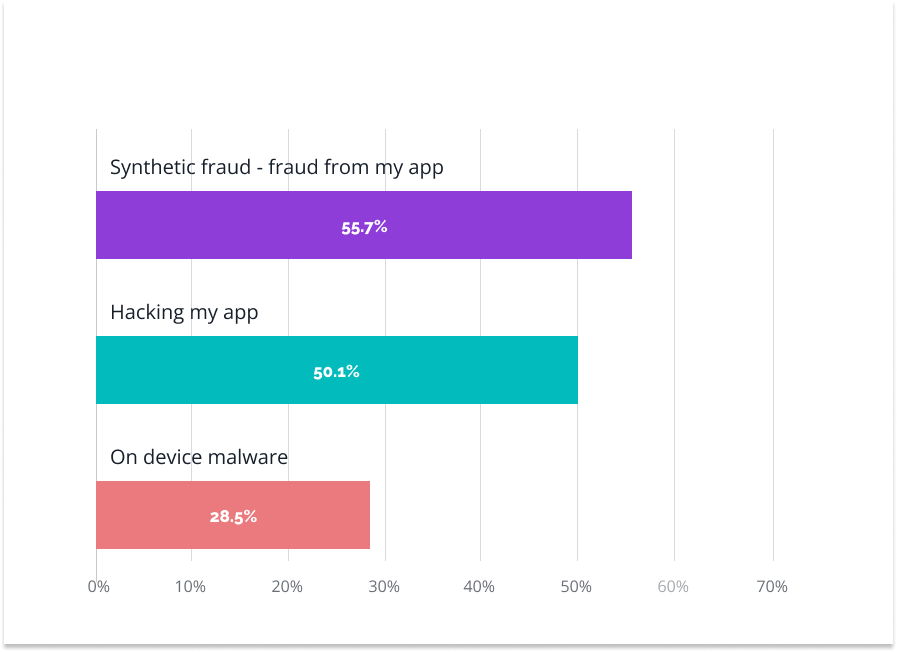
Source: https://www.statista.com/statistics/1381432/mobile-app-usage-cyber-threats-consumers-worldwide/
However, users are the last line of defense, and it is up to application developers and programmers to keep the software secure. So, let’s take a look at the most common threats an application can be exposed to:
- Man-in-the-Middle (MitM) attacks – the threat involves intercepting and possibly modifying communications between two parties without being a participant in those conversations. Such an attack usually aims to capture sensitive data, such as login details, credit card information, or other confidential messages.
- In-memory data attacks – the attack aims to gain access to sensitive data (e.g., passwords, credit card numbers, personal information) that is temporarily stored in the system or application memory (RAM).
- Threats related to authentication – authentication is the process of verifying the identity of a user or system. It is a crucial element in ensuring the security of any IT system, but it is also vulnerable to various types of attack – from brute force, where an attempt is made to guess a password by entering multiple combinations, to phishing, where an attempt is made to extract data by impersonating other people or institutions (such as banks).
Sometimes, drawing a clear line between the different types of threats is easy; other times, it can be a matter of using several techniques simultaneously (a perfect example is the combination of man-in-the-middle and phishing).
Unfortunately, we are seeing an increased trend in the different types of threats, and the worry is mainly caused by periodic spikes, which can mean testing new attacker software.
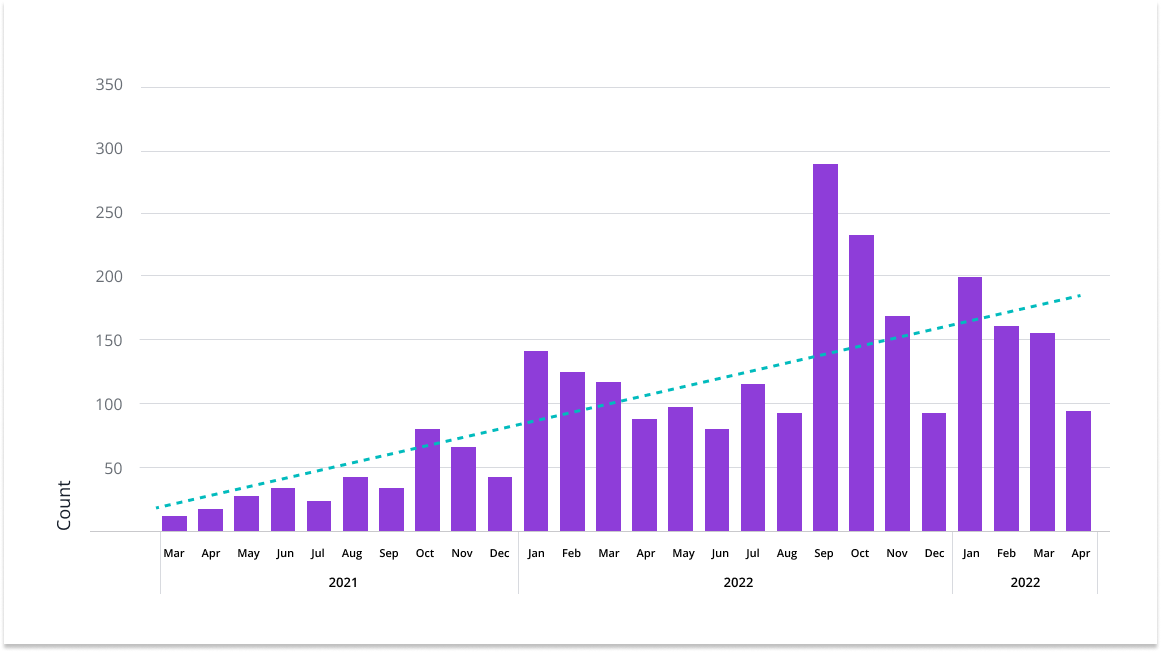
While the sheer number of attacks and their increasing sophistication may be a cause for concern, another side of the coin is the risk associated with scaling applications, which can introduce new weaknesses.
Why? The answer is simple – as the number of users, functionality, and integration with additional systems and services increases, the application architecture becomes more complex and challenging to monitor, and connecting to other systems, such as payment systems or databases, can create new entry points for potential attackers.
That’s why working from the bottom up is essential, laying the groundwork for future expansion.
Data Protection – how to secure users’ data
Data protection and quick response to possible security problems are the factors that most strongly influence the audience’s trust. And without it, it is difficult to talk about the application’s success.
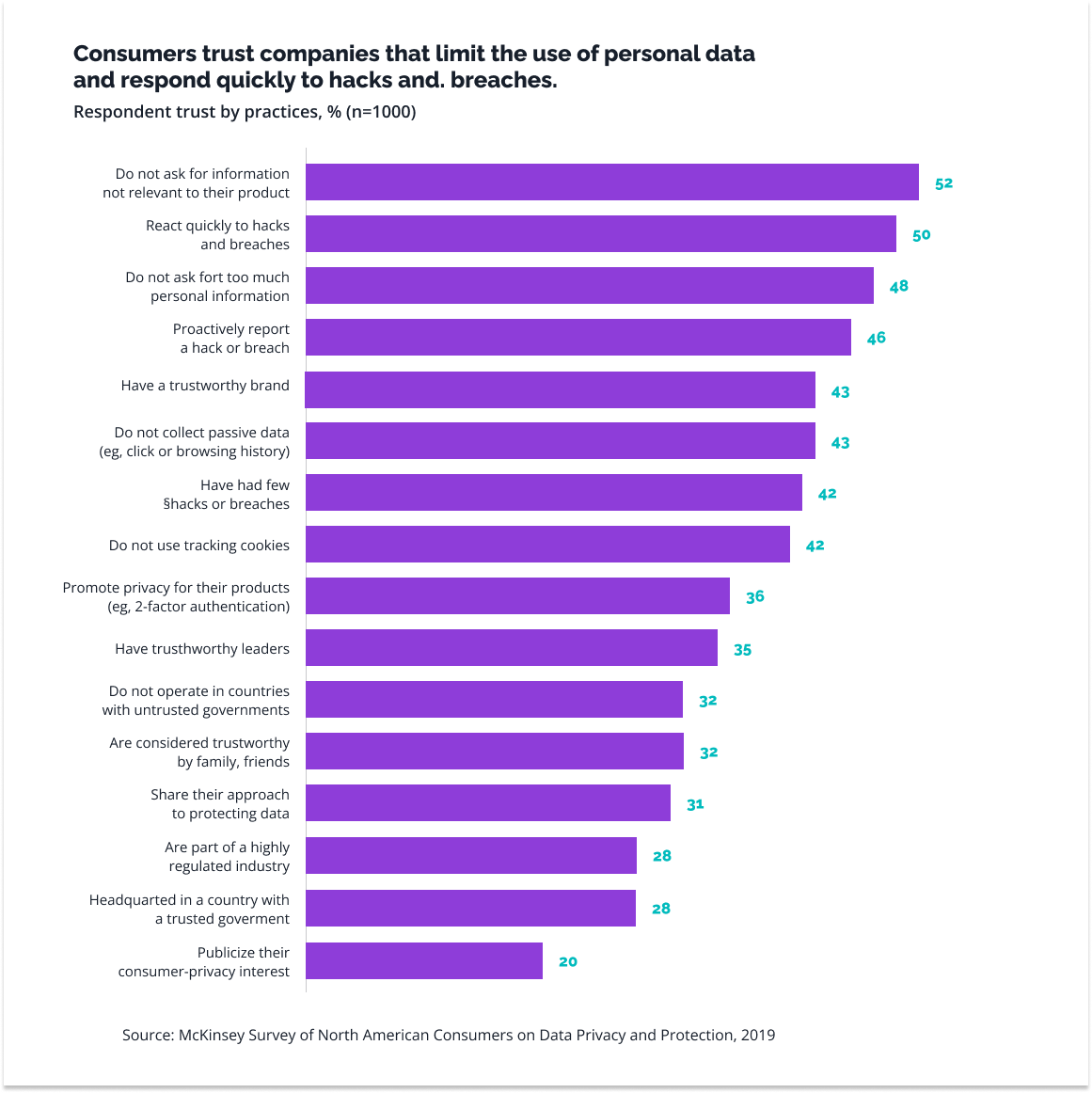
So, how can you effectively protect sensitive data? Implementing multiple defenses is best, as each acts as an additional firewall against potential threats. What are the options?
There are many, but we will focus on the most important ones:
DATA ENCRYPTION
Step one is data encryption – without it, you cannot even think about application security. Data encryption makes private information unreadable to outsiders, greatly increasing safety. And while it’s not a once-and-for-all solution, as it also needs to be monitored and updated, it is a foundation. Without data encryption, any hacker can easily access the data.
It might seem that ensuring data security is a priority for every company, yet we continue to hear stories about data breaches.
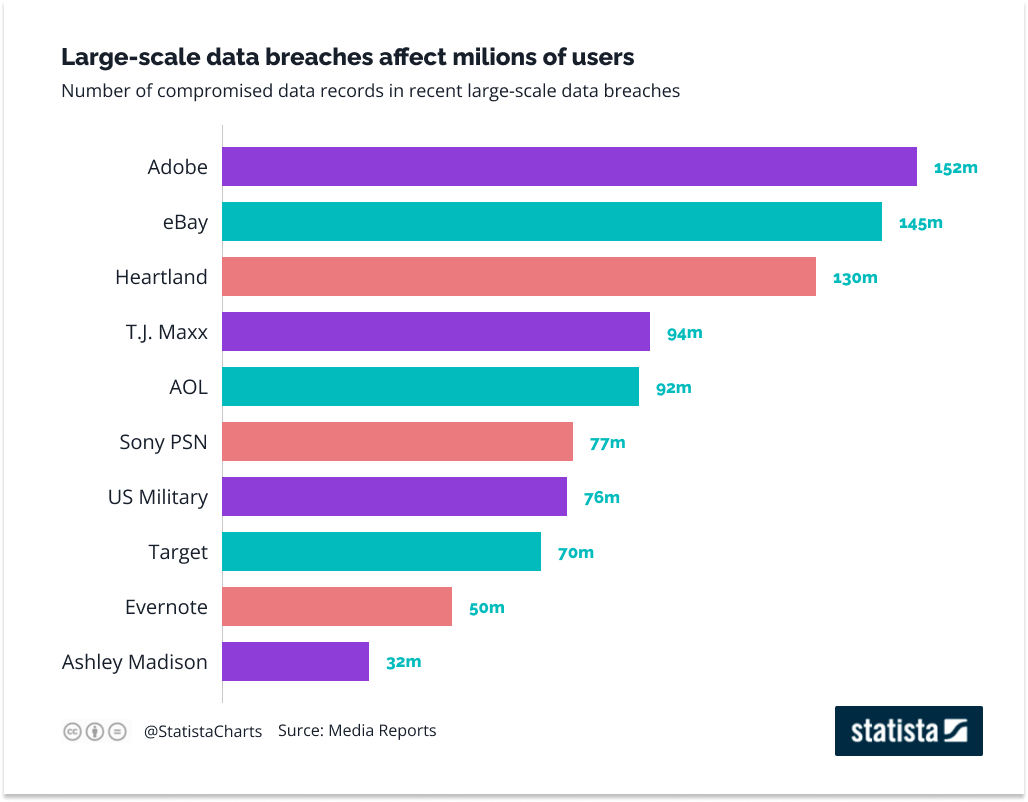
Source: https://www.statista.com/chart/2540/data-breaches/
While the biggest breaches in this area happened a few or a dozen years ago, when security was taken lightly, it’s easy to imagine the consequences of such a leak today! That’s why preventing data leaks is so important.
To avoid unpleasant situations, remember the following:
- Regular updates
- Multifactor authentication
- Strong password policies
- Education – both for employees and users
SECURE SESSION MANAGEMENT
Users who log into an application are given a kind of “access ticket”. This allows them to use the application freely but opens another door to various dangers. How do you counter them?
The base is the secure storage of access tokens, i.e., the use of mechanisms such as HTTP-only cookies, which restrict access to the server only, or the introduction of a short expiration time for access tokens, which makes them useful only for a short time.
In the second case, there may be a problem with an authorized user having to log in again after some time, but this inconvenience can be easily solved by introducing refresh tokens, which allow the user to extend the session without having to log in again, while still maintaining a high level of security.
AUTHENTICATION AND AUTHORIZATION
Authentication and authorization play a key role not only in applications developed in Flutter but in all digital systems and applications, and more and more developers are making users aware of this aspect.
Why? Because applications often process and store sensitive data, such as users’ personal information or financial data (e.g., payment card numbers). With authentication, only authorized people can access this data. Moreover, authentication can be used to customize the in-app experience, offering users tailored content or features for a more satisfying experience.
What are the best practices for secure user logins and password management? In our experience, these are the most effective:
- Two-factor authentication (2FA), where, in addition to a password, the user must provide a second verification code that can be generated by the application or sent via SMS or email. That way, even if a third party gets the password, they can’t log in without the second code.
- Strong passwords that force the user to create a combination of letters, numbers, and symbols.
- Automatic lockout after multiple failed access attempts.
- Audit and monitor the application status so that as the application evolves and new features are added, the authorization system can be adjusted to meet growing needs.
ATTACKS AND THE DEFENSE AGAINST THEM
Even the best security system cannot completely protect an application from at least attempted attacks from the outside, that is why it’s so important to be prepared to respond quickly in an emergency. The worst thing to happen during a cyberattack is panic and chaotic action.
So how can you prepare? First of all, procedures. To implement them, however, you need to know what you are defending against and how to do it, so here is a summary of the most common threats and examples of how to counter them.
MITM ATTACKS
Man-in-the-middle attacks intercept communications between two parties without their knowledge and can lead to phishing for sensitive data. The solution? Encryption and two-factor authentication will make the attackers’ job harder. It also is worthwhile to make users aware of such behavior, for example, by warning them not to click on suspicious links.
XSS AND CSRF ATTACKS
Cross-site scripting (XSS) involves inserting malicious scripts into pages that can then bypass specific user access controls. On the other hand, Cross-Site Request Forgery (CSRF) is an attack in which an attacker forces the victim’s browser to perform unwanted actions on the web application in which the victim is logged in. These two threats are often confused, but the specifics of the danger are less critical in the context of our article, which is primarily about protection.
So, how can you protect against these types of attacks? The use of tokens, which must be sent with every request to ensure that it comes from a valid source, and a Content Security Policy (CSP), which limits the possibility of malicious scripts, work well.
IN-MEMORY DATA ATTACKS
In mobile applications, data stored on the device, such as passwords or private keys, can be vulnerable to attacks that have earned the term in-memory data attacks. This is where Flutter’s standard solutions, including the flutter_secure_storage plugin, provide secure storage for keys and other sensitive information.
It’s also a good idea to limit the amount of time-sensitive data stored and to implement the encryption and authentication mentioned earlier.
By keeping these practices in mind, we can increase the security of our mobile applications developed in Flutter and protect our users’ sensitive data. Of course, the above examples are not exhaustive but are the most common. But again, the key is to provide multi-layered security, from encryption to system monitoring and updating.
Security testing
Most applications are developed in stages, with user feedback guiding the way. However, this principle does not apply to security, as gaps in this area can not only discourage users from using the application but can also lead to severe consequences, including legal ones.
That’s why it’s so important to test your security and, at a minimum, perform penetration tests and risk assessments. Working with Flutter, many of these tests can be automated, allowing you to manage your system more efficiently and react quickly when irregularities are detected.
Where to start? With a risk assessment – think about what data your application processes, where it is stored, what functions are most critical, and what components may be vulnerable to attack. We hope this article will help you make that assessment!
The next step is to determine the testing scope, i.e., the elements of the application to be tested. We know from experience that it can be difficult for developers to specify the testing area objectively, so sometimes, it is worth hiring an external company to perform a professional audit and point out possible threats and vulnerabilities.
Finally, documentation. While no one likes “paperwork,” carefully documented results allow you to work more efficiently, set a course of action, and monitor progress.
A lot of work? Yes, but we mentioned above that you can use many tools to make this phase easier. Among the most popular are:
- The SonarQube plugin can help you write cleaner, more secure code.
- OWASP ZAP and/or Burp Suite for real-time security testing.
- Dependabot to help monitor dependencies in a project for various vulnerabilities.
The list of available plugins is much longer, and many useful solutions can be found here.
Platform security
We’ve written a lot about the role of updates in keeping applications secure, but it takes two to tango, and not all users are eager for updates and will reject them indefinitely. This applies not only to updates to the applications themselves but even to operating systems, as a study conducted by Apple some time ago brilliantly demonstrated.
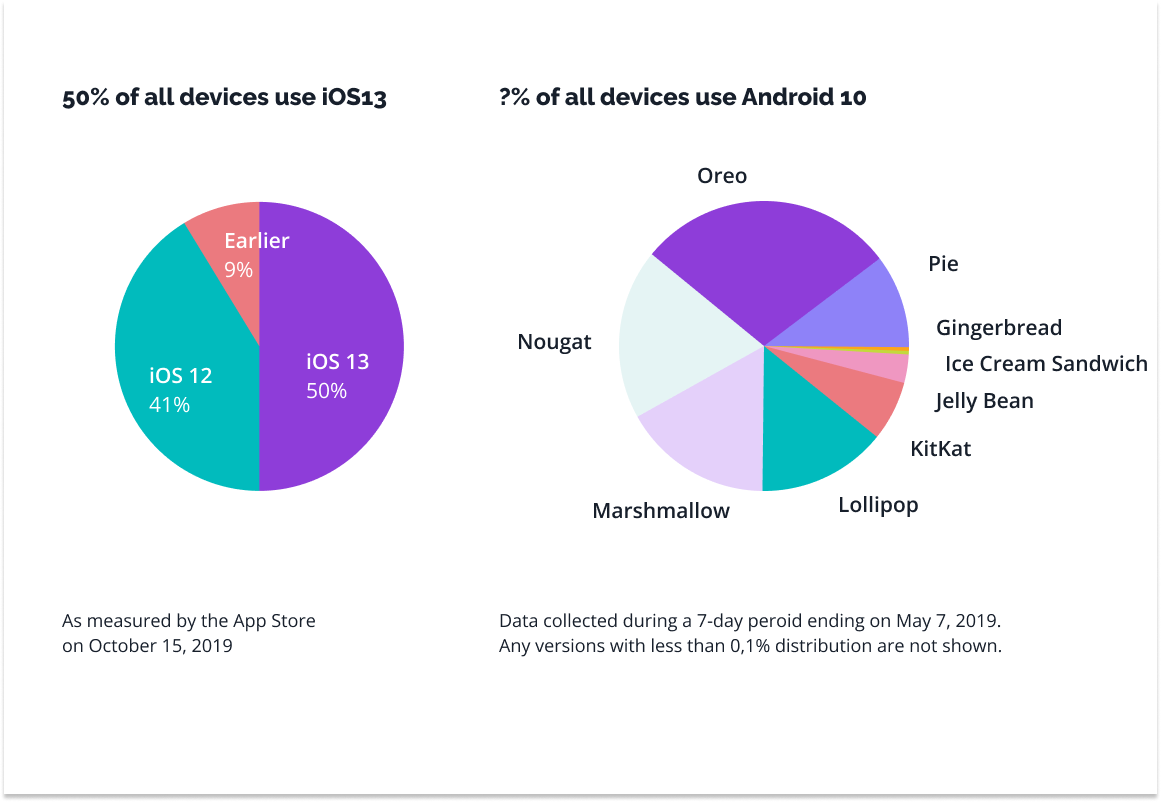
Source: https://venturebeat.com/mobile/as-ios-13-hits-50-adoption-android-fragmentation-keeps-getting-worse/
Such fragmentation is a real problem because it stratifies the security management process. Hence the importance of taking countermeasures. This can be done in various ways – and again, juggling several of them works best.
- Consistent versioning – communicate what the (new) version brings to the application, what it improves, or what bugs it fixes.
- When a critical security update is available, send notifications to users to inform them of the need to update.
- Before releasing an update, test it in a production environment to ensure you are not introducing new bugs or security vulnerabilities.
- Use official distribution channels – always publish your applications to official stores, such as Google Play or the Apple App Store, to minimize the risk of third-party modification.
- Respond to threats when the monitoring system detects a problem, even if it means temporarily disabling certain app features.
- Regularly review server and application logs for unexpected or suspicious activity, analyze them, and respond to unwanted activity.
Challenges and best practices in mobile application security
Mobile application security is not only key to protecting user data, it is also critical to a company’s reputation. In the digital age, where security breaches are highly publicized and can result in significant financial and reputational losses, organizations must pay close attention to the security of their applications. And the list of potential threats continues to grow.
While many risks and protections are common to all mobile applications, the specifics of Flutter require attention to the unique challenges of this platform. Due to the cross-platform nature of Flutter, developers need to be aware of both iOS and Android specifics and the potential risks associated with middleware interpreting Dart code.
Our company has many years of experience in this field – if you need help to increase the security of your application, contact us!




